Crayonic Device Manager: Enterprise Crayonic Device Management Platform and API Overview
Executive Summary
Crayonic Device Manager is a comprehensive enterprise security platform designed for monitoring, managing, and auditing Crayonic devices (Crayonic Badge, Crayonic KeyVault, Crayonic Bridge etc.) across MS Windows environments. The platform provides real-time security event monitoring, multi-tenant organization management, and comprehensive audit capabilities for enterprise security administrators. The platform can be deployed on-premises or in the cloud (Azure/AWS/GCP or private cloud), and provides a RESTful API for programmatic access and integration with other security tools (SIEM) and platforms such as Microsoft Entra ID, Microsoft Sentinel, Microsoft Security Copilot, etc.
Architecture Overview
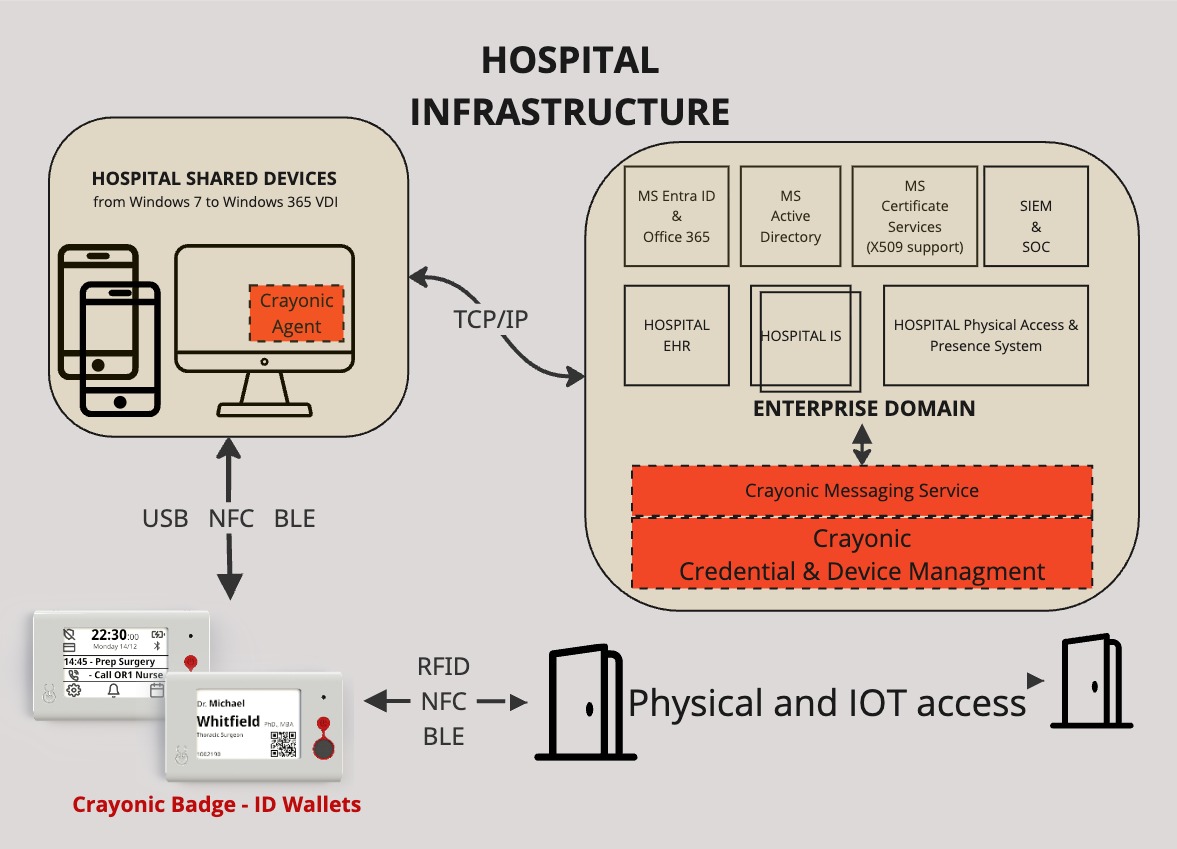
Three-Tier Architecture
- Windows Service Agent - Deployed on each monitored machine
- REST API Backend - Centralized data processing and management
- Web Administration Console - Browser-based management interface
┌─────────────────┐ ┌─────────────────┐ ┌─────────────────┐
│ Windows │ │ REST API │ │ Web Admin │
│ Service │───▶│ Backend │◀───│ Console │
│ Agent │ │ (Flask/MySQL) │ │ (React) │
└─────────────────┘ └─────────────────┘ └─────────────────┘
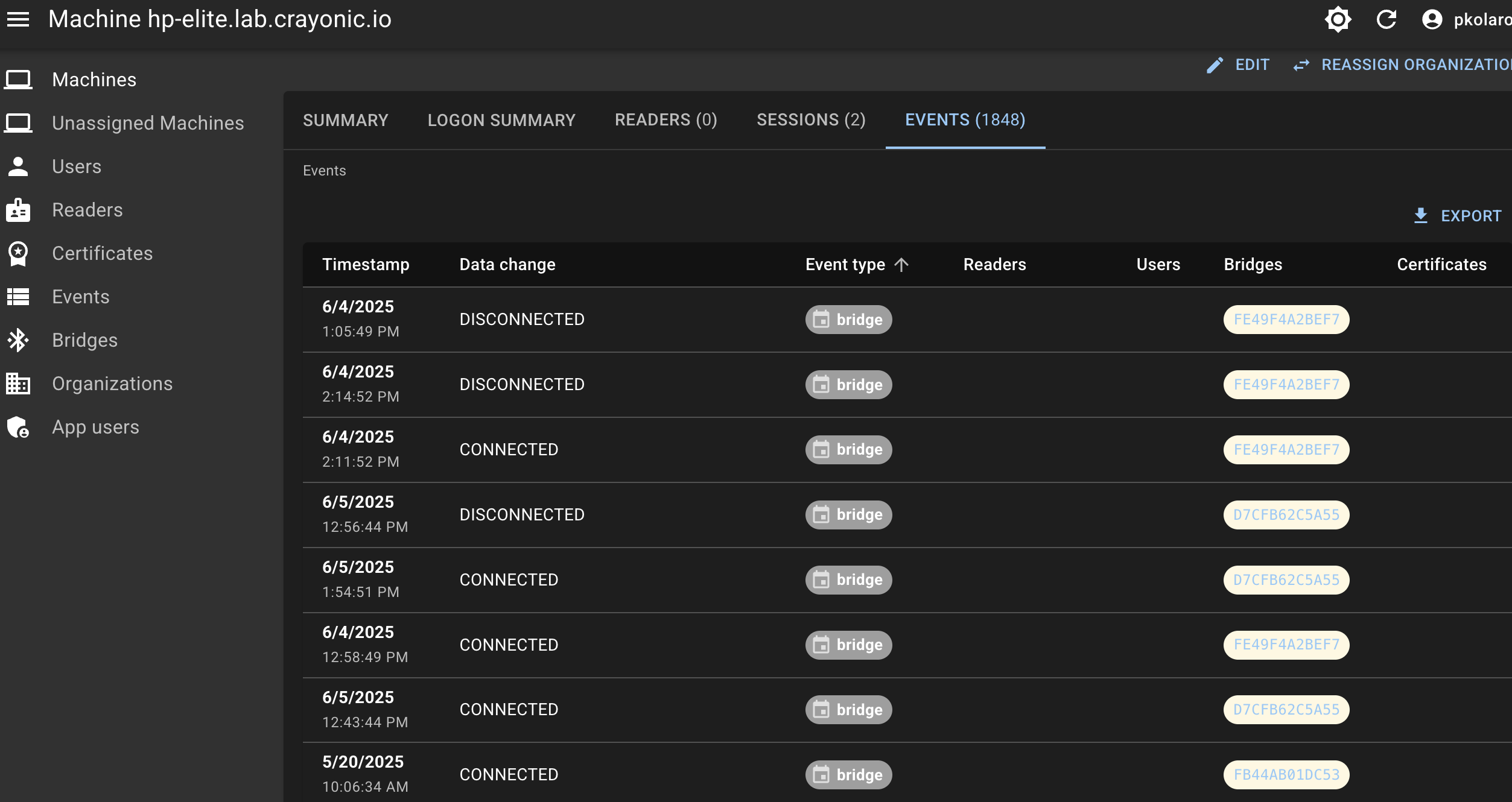
Web Admin view example of Crayonic Agent events in the Web Admin Console:
Core Security Features
Real-Time Security Event Monitoring
The Crayonic Agent continuously monitors and logs critical security events:
Authentication Events
- Smart Card Insertions/Removals: Real-time detection of PIV card usage
- User Session Events: Login, logout, lock, unlock, and session termination
- Certificate-Based Authentication: PKI certificate usage tracking
- Multi-Factor Authentication: FIDO2/WebAuthn security key operations
Device Security Events
- USB Device Monitoring: KeyVault device connection/disconnection
- Reader Status Changes: Smart card reader availability and status
- Device Firmware Updates: Automatic security patch deployment
- Hardware Tampering Detection: Unauthorized device modifications
System Security Events
- Workstation Lock/Unlock: Automatic workstation security enforcement
- Session Management: Active user session tracking and validation
- Service Health Monitoring: Agent availability and operational status
- Network Connectivity: Secure communication with management infrastructure
Advanced Security Capabilities
Automatic Workstation Locking
- Configurable automatic workstation lock when KeyVault devices are removed
- Prevents unauthorized access to unattended workstations
- Customizable timeout and security policies
Certificate Management
- Real-time PKI certificate discovery and validation
- Certificate expiration monitoring and alerting
- Integration with enterprise certificate authorities
- Automated certificate lifecycle management
Firmware Security Management
- Automatic firmware update deployment from secure repositories
- Version control and rollback capabilities
- Security patch management for KeyVault devices
- Centralized firmware policy enforcement
Multi-Tenant Organization Management
Enterprise-Grade Isolation
Organization Structure
- Complete Data Isolation: Each organization sees only their data
- Hierarchical Access Control: Multiple levels of administrative access
- Cross-Organization Security: Prevents data leakage between tenants
- Scalable Architecture: Support for unlimited organizations on single instance
Role-Based Access Control (RBAC)
System-Level Roles: - Superadmin: Global system access, organization creation/deletion - Admin: System-level access, user management - User: Standard system access
Organization-Level Roles: - org_admin: Organization administration, user management within org - org_user: Standard organization member access - org_viewer: Read-only organization access
Security Boundaries
- Machine Isolation: Users only access machines in their organizations
- Event Isolation: Security events filtered by organization membership
- User Isolation: Administrative access limited to organization scope
- Audit Isolation: Compliance reporting scoped to organization boundaries
Use Cases for Security Administrators
1. Compliance and Audit Management
Regulatory Compliance
- SOX Compliance: Detailed audit trails for financial system access
- HIPAA Compliance: Healthcare data access monitoring and reporting
- PCI DSS: Payment card industry security requirement enforcement
- GDPR Compliance: Data access tracking and privacy controls
Audit Capabilities
- Comprehensive Event Logging: All security events with timestamps and context
- User Activity Tracking: Detailed logs of user authentication and access
- Device Usage Reports: Smart card and security key utilization analytics
- Timeline Analysis: Chronological security event reconstruction
- Export Capabilities: Audit data export for compliance reporting
2. Incident Response and Forensics
Security Incident Investigation
- Real-Time Alerting: Immediate notification of security events
- Event Correlation: Link related security events across multiple machines
- Timeline Reconstruction: Detailed chronological event analysis
- User Behavior Analysis: Identify anomalous authentication patterns
- Device Tracking: Monitor specific KeyVault device usage across organization
Forensic Analysis
- Immutable Audit Logs: Tamper-evident security event storage
- Chain of Custody: Detailed tracking of device and certificate usage
- Cross-Reference Analysis: Correlate events across users, machines, and devices
- Historical Analysis: Long-term security trend identification
3. Access Control and Identity Management
Privileged Access Management
- Administrative Access Monitoring: Track privileged user activities
- Certificate-Based Authentication: Enforce PKI-based access controls
- Multi-Factor Authentication: Monitor MFA compliance and usage
- Session Management: Real-time tracking of active user sessions
Identity Lifecycle Management
- User Onboarding: Automated device provisioning and access assignment
- Access Reviews: Regular audit of user permissions and device assignments
- Offboarding: Secure removal of access and device decommissioning
- Role Changes: Track and audit role modifications and access changes
4. Risk Management and Security Operations
Threat Detection
- Anomaly Detection: Identify unusual authentication patterns
- Unauthorized Access Attempts: Monitor failed authentication events
- Device Tampering: Detect hardware security violations
- Policy Violations: Identify non-compliant security behaviors
Security Policy Enforcement
- Device Policy Management: Centralized security policy deployment
- Compliance Monitoring: Real-time policy adherence verification
- Automated Remediation: Automatic response to security policy violations
- Risk Scoring: Quantitative risk assessment based on security events
Technical Implementation
Deployment Architecture
Agent Deployment
- Windows Service: Runs as system service with elevated privileges
- Minimal Footprint: Low resource consumption and network overhead
- Secure Communication: Encrypted communication with management infrastructure
- Offline Capability: Local event storage during network outages
Centralized Management
- Cloud-Ready: Azure or private cloud (Kubernetes) deployment with auto-scaling capabilities
- High Availability: Redundant infrastructure with failover capabilities
- Secure APIs: RESTful APIs with OAuth2 and JWT authentication
- Database Security: Encrypted data storage with access controls
Integration Capabilities
Enterprise Integration
- Active Directory: Integration with existing identity management systems
- SIEM Integration: Export security events to enterprise SIEM platforms
- API Access: RESTful APIs for custom integrations and automation
- Single Sign-On: OAuth2 integration with Microsoft Entra ID, and other providers
Monitoring and Alerting
- Real-Time Dashboards: Live security event monitoring and visualization
- Custom Alerts: Configurable alerting based on security event patterns
- Reporting Engine: Automated compliance and security reports
- Notification Systems: Email, SMS, and webhook notification capabilities
Security and Privacy
Data Protection
- Encryption at Rest: All stored data encrypted using industry-standard algorithms
- Encryption in Transit: TLS 1.3 for all network communications
- Access Controls: Role-based access with principle of least privilege
- Data Retention: Configurable retention policies for compliance requirements
Privacy Controls
- Data Minimization: Only collect necessary security-relevant data
- Anonymization: Option to anonymize personal identifiers in logs
- Right to Erasure: Capability to remove user data upon request
- Consent Management: Granular consent controls for data collection
Getting Started
Prerequisites
- Windows 10/11 for agent deployment
- MySQL 8.0+ or compatible database for backend
- Modern web browser for administration console
- Network connectivity for centralized management
Deployment Steps
- Infrastructure Setup: Deploy backend services and database
- Agent Installation: Install Windows service on monitored machines
- Organization Configuration: Set up organizations and user roles
- Device Assignment: Assign machines to appropriate organizations
- Policy Configuration: Configure security policies and alerting rules
Support and Documentation
- Technical Documentation: Comprehensive API and configuration guides
- Training Materials: Administrator training
- Professional Services: Implementation and customization services
- 24/7 Support: Enterprise support with SLA guarantees
Event Types and Data Collection
Detailed Event Categories
User Session Events
{
"event_type": "user",
"change": "WTS_SESSION_LOGON",
"session_info": {
"UserName": "john.doe",
"LogonDomain": "ENTERPRISE",
"SessionId": 1,
"State": "Active"
},
"workstation_locked": false,
"timestamp": 1704067200
}
Device Connection Events
{
"event_type": "reader",
"change": "PLUGGED_IN",
"device_id": "CRAY-KV-001234",
"device_info": {
"firmware_version": "1.2.3",
"hardware_version": "2.1",
"battery_level": 85,
"interface_type": "PIV"
},
"timestamp": 1704067200
}
Certificate Events
{
"event_type": "certificate",
"change": "CERTIFICATE_DETECTED",
"certificate_info": {
"serial_number": "1A2B3C4D5E6F",
"issuer": "Enterprise CA",
"subject": "CN=John Doe,OU=IT,O=Enterprise",
"upn": "john.doe@enterprise.com",
"expiration": "2025-12-31"
},
"timestamp": 1704067200
}
Security Event Monitoring
Critical Security Events
- Unauthorized Device Access: Detection of unknown or unauthorized KeyVault devices
- Certificate Violations: Invalid, expired, or revoked certificate usage attempts
- Session Anomalies: Unusual login patterns or session behaviors
- Policy Violations: Non-compliance with organizational security policies
- Hardware Tampering: Physical security violations or device modifications
Compliance Events
- Access Logging: Detailed logs of all system and data access attempts
- Authentication Tracking: Multi-factor authentication usage and compliance
- Data Access Auditing: Tracking of sensitive data access with user attribution
- Policy Enforcement: Real-time monitoring of security policy adherence
API Reference for Integration
Authentication Endpoints
POST /auth/login
POST /auth/logout
POST /auth/refresh
GET /auth/token
Organization Management
GET /organizations
POST /organizations
PUT /organizations/{id}
DELETE /organizations/{id}
GET /organizations/{id}/users
POST /organizations/{id}/users
Security Event APIs
GET /events
GET /events/{id}
GET /machines/{id}/events
GET /users/{id}/events
POST /events/search
Device Management
GET /machines
GET /machines/{id}
PUT /machines/{id}
GET /machines/unassigned
POST /machines/{id}/assign-organization
Implementation Examples
PowerShell Integration
# Query recent security events
$headers = @{
'Authorization' = "Bearer $token"
'Content-Type' = 'application/json'
}
$events = Invoke-RestMethod -Uri "https://api.crayonic.io/events" `
-Headers $headers -Method GET
# Filter for authentication events
$authEvents = $events | Where-Object {
$_.event_type -eq "user" -and
$_.data.change -like "*LOGON*"
}
SIEM Integration Example
import requests
import json
def export_security_events(start_time, end_time):
"""Export security events for SIEM ingestion"""
headers = {
'Authorization': f'Bearer {api_token}',
'Content-Type': 'application/json'
}
params = {
'start_time': start_time,
'end_time': end_time,
'event_type': 'security'
}
response = requests.get(
'https://api.crayonic.io/events',
headers=headers,
params=params
)
return response.json()
Troubleshooting and Maintenance
Common Issues and Solutions
Agent Connectivity Issues
- Symptom: Agent not reporting events to central server
- Solution: Check network connectivity, firewall rules, and certificate validity
- Diagnostic: Review agent logs in Windows Event Viewer
Authentication Failures
- Symptom: Users unable to access web console
- Solution: Verify OAuth2 configuration and user organization assignments
- Diagnostic: Check JWT token validity and user permissions
Performance Optimization
- Database Indexing: Ensure proper indexes on timestamp and organization_id fields
- Event Filtering: Configure appropriate event retention policies
- Resource Monitoring: Monitor CPU and memory usage on agent machines
Maintenance Procedures
Regular Maintenance Tasks
- Database Cleanup: Remove old events based on retention policy
- Certificate Renewal: Update SSL/TLS certificates before expiration
- Agent Updates: Automatic rolling window agent updates during maintenance windows
- Backup Verification: Verify database backups and recovery procedures
Security Hardening
- Access Review: Quarterly review of user access and permissions
- Vulnerability Scanning: Regular security scans of infrastructure
- Penetration Testing: Annual security assessments
- Compliance Audits: Regular compliance verification and reporting